Best Practices for Managing API Access in Zendesk
What are the best practices for managing API access in Zendesk Suite?
Managing API access in Zendesk Suite involves several best practices. It's important to disable password access to your API to limit exposure to sensitive information. Admins should set up least privilege access to reduce the number of people with API access. Using OAuth clients can secure API access, and it's recommended to choose the right flow type for your use case, preferring Authorization Code Grant or Implicit Grant over Password Grant.
More related questions
How can I enhance password security in Zendesk Suite?
Enhancing password security in Zendesk Suite is crucial for protecting your account. You can customize your password security level to align with your internal policies. Zendesk offers several levels of password security: Recommended, High, Medium,…
What is the purpose of two-factor authentication in Zendesk Suite?
Two-factor authentication (2FA) adds an extra layer of security to your Zendesk Suite account. It requires users to provide two forms of identification before accessing their account, which can be done via SMS or a 2FA app on a mobile device. This…
How can I restrict access to Zendesk Suite using IP addresses?
Restricting access to Zendesk Suite by IP addresses is a great way to enhance security. You can limit the agent interface to users coming from a specific range of approved IP addresses. This ensures that only authorized users from trusted networks…
What are the benefits of using Single Sign-On (SSO) in Zendesk Suite?
Single Sign-On (SSO) in Zendesk Suite simplifies the login process by allowing users to access multiple applications with a single set of credentials. This reduces the number of attack surfaces and enhances security by minimizing the need for…
How can I manage email security in Zendesk Suite?
Managing email security in Zendesk Suite involves several practices. You can archive customer communications for auditing purposes, disable rich content in emails, and decommission unused support email addresses. Additionally, enabling email…
What is the role of malware scanning in Zendesk Suite?
Malware scanning in Zendesk Suite is essential for managing attachments that may pose a security risk. Admins should follow company guidelines to handle attachments flagged by the malware scanning feature. This proactive approach helps protect your…
How can I use Zendesk's sandbox environment effectively?
Using Zendesk's sandbox environment is recommended for testing and launching code before it goes into your production environment. This allows you to experiment with new features and configurations without affecting your live setup. Note that the…
How can I ensure secure attachment access in Zendesk Suite?
To ensure secure attachment access in Zendesk Suite, you can require users to log in to their account before accessing attachments by activating private attachments. This measure helps protect sensitive information and ensures that only authorized…
What is the importance of device tracking in Zendesk Suite?
Device tracking in Zendesk Suite is important for managing user devices and ensuring that only authorized devices have access to your account. Admins can remove devices that are no longer in use, which helps maintain security by preventing…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
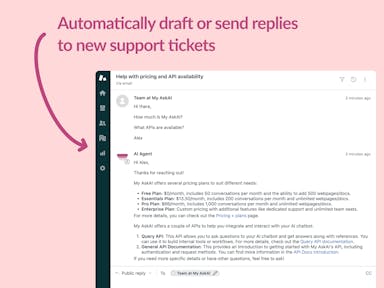

Zendesk Messaging (live chat)
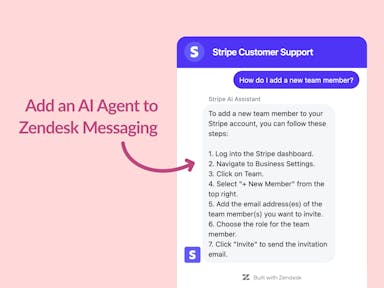
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

