What email encryption protocols does Zendesk support?
What email encryption protocols does Zendesk support?
Zendesk supports opportunistic-TLS as an end-to-end email encryption protocol. This means that Zendesk will accept or send TLS-encrypted emails if the sending or recipient server also supports that protocol. Opportunistic-TLS is a widely used encryption method that ensures emails are encrypted during transmission if both parties support it.
For more details on email encryption protocols supported by Zendesk, check out theoriginal article.
More related questions
Can Zendesk handle encrypted emails?
Zendesk can handle encrypted emails, but with limitations. While Zendesk can process emails that arrive in an encrypted state, it cannot decrypt them. This is because decryption requires authentication and the necessary identity, which Zendesk does…
How do private email relays work with Zendesk?
Private email relays work with Zendesk by obscuring the sender's identity. These services use tokenized Reply-To addresses, which means the original sender's email address is replaced with a proxy address. This ensures privacy but can sometimes…
Can Zendesk decrypt emails or identify masked senders?
Zendesk cannot decrypt emails or identify masked senders. Decrypting emails or determining the identity of a masked sender is not only technically challenging but also against Zendesk's security and privacy policies. Attempting to do so could…
What are the common email encryption methods used today?
The most common email encryption methods used today are S/MIME and PGP/MIME. S/MIME is widely used and integrated into many large email providers like OSX, iOS, Outlook, and Gmail. PGP/MIME, on the other hand, relies on a decentralized model and…
Does Zendesk offer email address masking features?
Currently, Zendesk does not offer features to mask or obscure end-users' email identities. While you can set Support User Roles or restrict agent access through Custom User Roles on Enterprise plans, email address masking is not available. For more…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
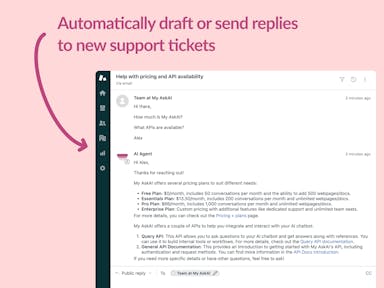

Zendesk Messaging (live chat)
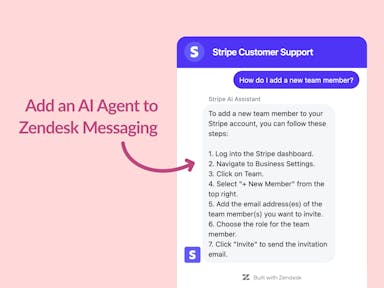
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

