Zendesk's Incident Response for Security Breaches
What is Zendesk's incident response process for security breaches?
Zendesk has a comprehensive incident management process for handling security events. This process includes a response time under which Zendesk will notify subscribers within 48 hours of verifying a security incident affecting your service data. The incident response program involves 24/7 monitoring systems and on-call staffing to address service incidents promptly. The process also outlines procedures for notification, escalation, mitigation, and documentation.
More related questions
How does Zendesk protect my service data during transmission?
Zendesk uses encryption to protect your service data during transmission. They maintain commercially reasonable safeguards, including encryption of service data at rest and in transmission using TLS or similar technologies. This ensures the…
How does Zendesk manage access control and privilege management?
Zendesk restricts administrative access to production systems to approved personnel only. Each person is assigned unique IDs and cryptographic keys or complex ephemeral tokens to authenticate and track their activities. Access rights are based on…
What security measures does Zendesk implement for data centers?
Zendesk's data centers employ robust security measures to protect service data. These include a dedicated security organization operating 24/7, restricted access to areas with system components, and industry-standard security policies….
How does Zendesk ensure third-party service providers protect service data?
Zendesk requires third-party service providers to implement appropriate technical and organizational security measures. These include physical access controls, system access controls, data access controls, transmission controls, input controls,…
What certifications and audits does Zendesk offer for security compliance?
Zendesk provides information on its compliance with security obligations through certifications and audits. Upon request, Zendesk can share its ISO 27001 certification and/or SOC 2 or SOC 3 reports with subscribers, provided they are not…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
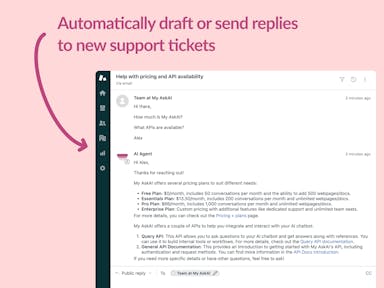

Zendesk Messaging (live chat)
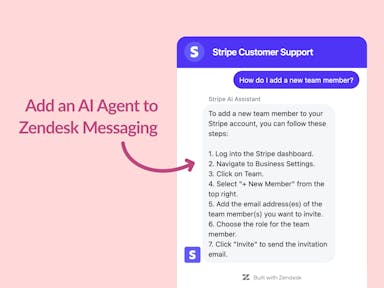
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

