Zendesk's Approach to Application Security
How does Zendesk handle application security?
Zendesk prioritizes application security by following a Secure Development Lifecycle. This includes training developers, conducting design and code reviews, and employing third-party security experts for penetration testing.
These steps help Zendesk identify and mitigate security threats, ensuring the safety of your data across its applications. By maintaining a proactive approach to application security, Zendesk protects your business interactions from potential vulnerabilities.
More related questions
How does Zendesk ensure data security for its customers?
Zendesk ensures data security by implementing robust encryption methods. Communications between customers and Zendesk servers are encrypted using HTTPS and TLS, ensuring secure access to your Zendesk subdomains. Additionally, data at rest is…
What physical security measures does Zendesk implement?
Zendesk implements stringent physical security measures to protect customer data. The company operates in data centers certified with ISO 27001, PCI/DSS Service Provider Level 1, and SOC II compliance, ensuring high standards of security. These…
What network security measures are in place at Zendesk?
Zendesk maintains a globally-distributed Security team that monitors network security 24/7. The team uses network vulnerability scanning, intrusion detection, and prevention systems to safeguard customer data. Additionally, Zendesk participates in…
How does Zendesk ensure business continuity and availability?
Zendesk ensures business continuity and availability through its Disaster Recovery program. This program includes service clustering and network redundancies to eliminate single points of failure, ensuring services remain available or are easily…
What product security features does Zendesk offer?
Zendesk offers a range of product security features to help administrators manage access and sharing policies. These include authentication and single-sign on (SSO) options, two-factor authentication, and IP restrictions. All communications with…
How can Zendesk access customer data for troubleshooting?
Zendesk can access customer data for troubleshooting purposes only when granted permission by an account administrator. This access is known as account assumption and is deactivated by default. Administrators can activate access for a specific…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
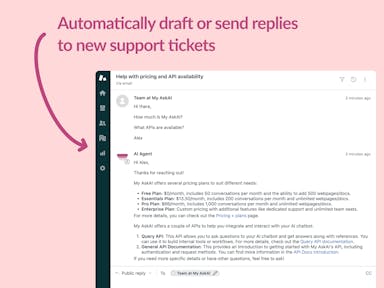

Zendesk Messaging (live chat)
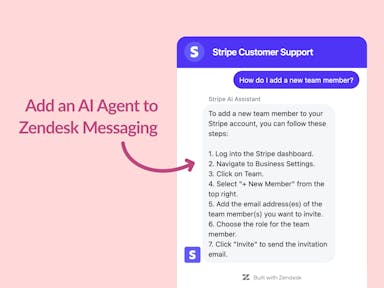
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

