Zendesk Security Settings Overview
What are the security settings available in Zendesk?
Zendesk offers various security settings to protect your data and user access. These include configuring the password security level, enabling two-factor authentication, and setting IP restrictions. These features help ensure that only authorized users can access your Zendesk Suite, enhancing overall security.
For a comprehensive guide on configuring these security settings, visit theZendesk help documentation.
More related questions
What authentication methods does Zendesk offer?
Zendesk provides several authentication methods to ensure secure access for both team members and end users. These include the standard Zendesk sign-in using email and password, third-party authentication through services like Google and Microsoft,…
How does Zendesk ensure security for team members?
To maintain security, Zendesk requires team members to be signed in and authenticated to access any part of the Zendesk Suite. Once signed in, team members can access the products they have permissions for via the product tray. This ensures that…
Do end users need to sign in to use Zendesk Support?
End users may or may not need to sign in to use Zendesk Support, depending on how you configure access. You can require end users to sign in and authenticate to use your help center and submit support requests via the support request form. This…
Can Zendesk Support be embedded into websites and apps?
Yes, Zendesk Support can be embedded into your websites and mobile apps. This feature allows you to integrate support directly into your digital platforms, providing a seamless experience for users. You also have the option to require end users to…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
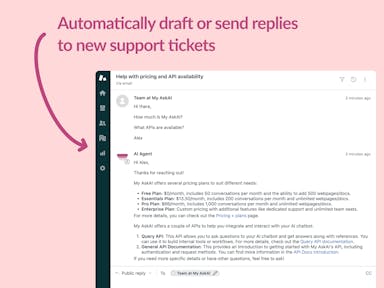

Zendesk Messaging (live chat)
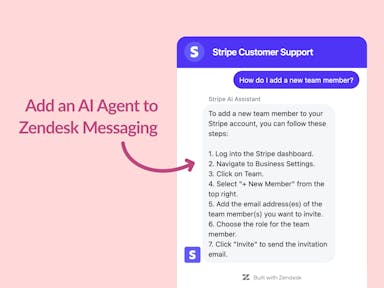
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

