Example Scenarios for Using Zendesk Access Log API
What are some example scenarios for using the Access Log API?
The Access Log API can be used in various scenarios, such as defining permissions and addressing security risks. For instance, an IT security manager can use access logs to ensure agents view only the data they are authorized to see, complying with data privacy regulations.
Additionally, access logs can help identify suspicious behavior, like repeated searches for sensitive information, allowing security teams to investigate and address potential risks proactively. These logs are invaluable for refining security policies and supporting compliance efforts.
More related questions
What is the Access Log API in Zendesk?
The Access Log API is a tool that captures data access events by agents or admins in your Zendesk account over the last 90 days. It provides a comprehensive log of what data has been accessed, such as tickets, user profiles, and searches, but does…
How do I enable the Access Log API in Zendesk?
To enable the Access Log API, you need to activate it in the Admin Center. Once activated, Zendesk will start capturing access events, but note that events prior to activation won't be recorded. To turn it on, navigate to the Admin Center, click on…
What kind of data does the Access Log API capture?
The Access Log API captures data access events by agents or admins, such as viewing tickets, user profiles, and searches. It records instances where data is accessed but not modified. This differs from the audit log, which tracks changes made to…
Why is the Access Log API important for data security?
The Access Log API is crucial for data security as it provides a detailed record of what data agents and admins access, helping to ensure compliance with data privacy regulations. By monitoring access events, you can identify unauthorized access or…
Can I export access logs from Zendesk?
Yes, you can export access logs from Zendesk using the Access Log API. This feature allows you to export a comprehensive log of access events for further analysis. Exporting access logs typically requires some developer experience, as you'll need…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
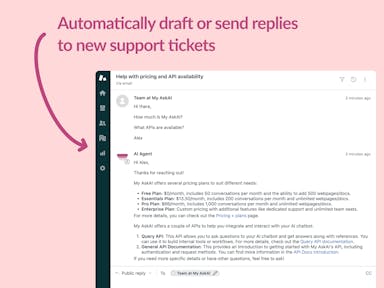

Zendesk Messaging (live chat)
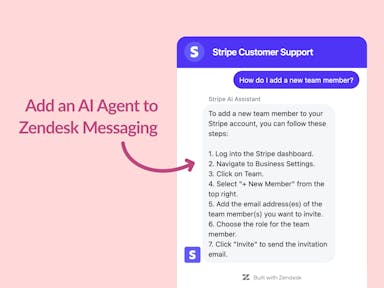
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

