Creating a Zendesk Bug Bounty Report
What should be included in a Zendesk Bug Bounty report?
A Zendesk Bug Bounty report should include several key pieces of information. You need to provide the vulnerable URL, any applicable vulnerable parameters, the type of vulnerability, and a detailed description of the issue. Additionally, include steps to reproduce the issue, and if possible, screenshots or a video demonstration. An example attack scenario can also help in demonstrating the risk and resolving the issue faster.
More related questions
What is the Zendesk Bug Bounty Program?
The Zendesk Bug Bounty Program is an initiative to engage with security researchers to report vulnerabilities. Zendesk is committed to security and privacy, and they validate, respond, and fix vulnerabilities reported responsibly. They assure that…
How can I participate in the Zendesk Bug Bounty Program?
To participate in the Zendesk Bug Bounty Program, you need to report any discovered security vulnerabilities. Start by signing up for an account at hackerone.com if you don't have one. Then, file a report detailing the suspected vulnerabilities….
What happens after I submit a vulnerability report to Zendesk?
After submitting a vulnerability report to Zendesk, their Security Ops team will evaluate it and inform you of the status. Reports that demonstrate valid security-related behavior but carry acceptable risk will be closed as informative. Identical…
Will I receive a reward for reporting a vulnerability to Zendesk?
You may receive a reward for reporting a vulnerability to Zendesk if you are the first to submit a report for a valid vulnerability. The Zendesk team will contact you to discuss the conditions of the bounty. However, duplicate reports will not be…
Interested indeflectingover 70% of your Zendesk support tickets?

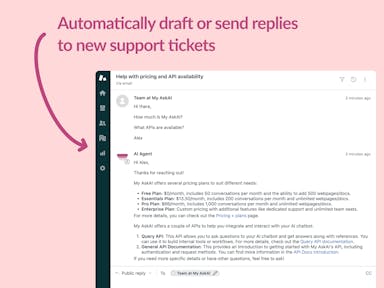
Zendesk Support Tickets

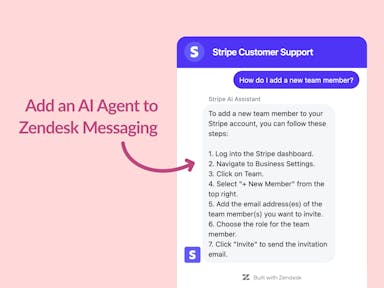
Zendesk Messaging (live chat)
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

