Actions for Zendesk Users on Log4j Vulnerability
Do Zendesk users need to take any action regarding the Log4j vulnerability?
Users of Zendesk services do not need to take any action at this time concerning the Log4j vulnerability. However, users of custom products developed under Professional Services agreements should review their agreements and validate their use of the Log4j component. It's also recommended that customers evaluate their own use of the Apache Log4j library in any custom apps or integrations and upgrade to a fixed version if a vulnerable version is identified.
More related questions
What is the Apache Log4j vulnerability (CVE-2021-44228)?
The Apache Log4j vulnerability, also known as CVE-2021-44228, is a serious security flaw in the popular Java logging library, Log4j. This vulnerability allows an unauthenticated attacker to execute code on systems using this library by sending…
How has Zendesk addressed the Log4j vulnerability?
Zendesk has taken significant steps to mitigate the Log4j vulnerability within its products. Upon discovery, Zendesk activated its incident response process, identified all Log4j deployments, and applied vendor-provided updates or recommended…
Did Zendesk investigate other Log4j vulnerabilities like CVE-2021-45046 and CVE-2021-45105?
Yes, Zendesk investigated additional Log4j vulnerabilities, specifically CVE-2021-45046 and CVE-2021-45105. A risk assessment was conducted, and actions were taken where significant risks were identified. Notably, CVE-2021-45105 is a Denial of…
Where can I find more information about the Log4j vulnerability?
For more detailed information about the Log4j vulnerability, you can refer to resources provided by the Apache Software Foundation and the National Vulnerability Database. These sources offer comprehensive insights into the nature and impact of the…
Interested indeflectingover 70% of your Zendesk support tickets?

Zendesk Support Tickets
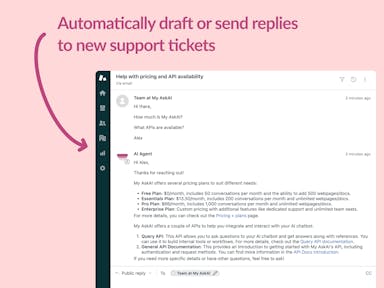

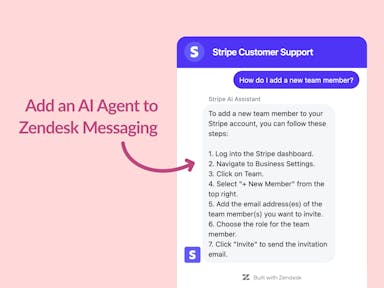
Zendesk Messaging (live chat)
Join1,000+ companies reducing their support costs and freeing up support agents for more important work
“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy
“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc
“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)

“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash

“We needed an AI agent integrated within our current tools. My AskAI was the only solution that wasn't going to disrupt our operations.”
Zeffy

“At the end of last year I was given the challenge - how can we provide the same or better service, without hiring anyone?”
Zinc

“My AskAI blew everybody else out of the water. It made the selection process very easy for us.”
Customer.io($50M+ ARR)
“It now resolves 71% of queries (over 35,000 every month), meaning more time solving complex issues and improving UX.”
Freecash







Reduce support costs.Spend more time on customer success.

